In a digital age dominated by online interactions, protecting personal information is more crucial than ever. Regrettably, user credentials frequently end up on the dark web, posing significant threats. It’s essential to comprehend the path of stolen credentials and the significance of dark web credential monitoring in fortifying cybersecurity defenses.
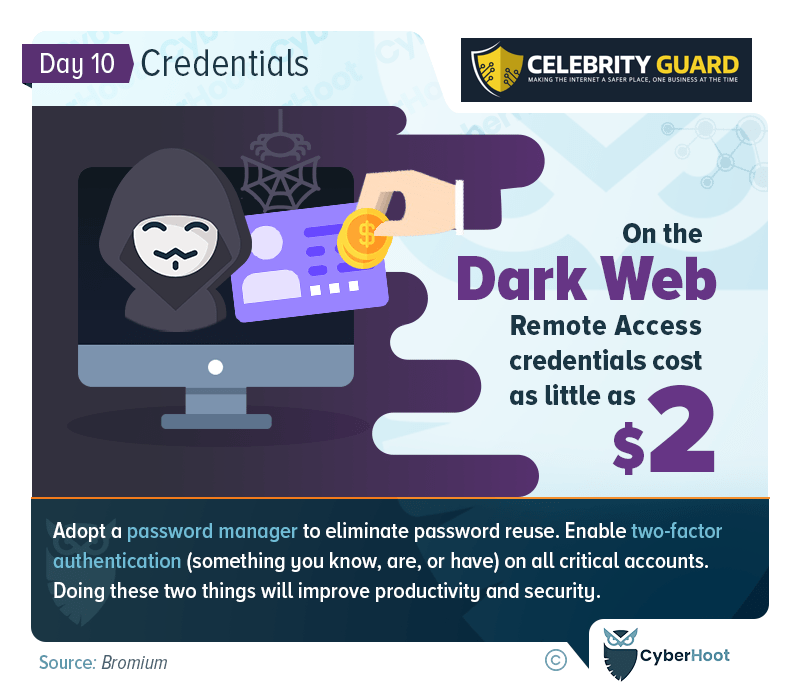
Decoding the Path to the Dark Web: How User Credentials are Compromised
- Originating from Data Breaches: The primary source of pilfered user credentials stems from data breaches. Cybercriminals exploit vulnerabilities in security systems to gain unauthorized access to databases containing sensitive information across various sectors.
- Credential Stuffing Shenanigans: Once hackers obtain a set of usernames and passwords, they engage in credential stuffing attacks. Automated tools try these credentials across multiple platforms, capitalizing on the common practice of password reuse.
- Phishing Ploys: Phishing remains a prevalent method for stealing user credentials. Cybercriminals craft deceptive emails, messages, or websites to trick individuals into revealing their login details, turning the stolen information into a commodity on the dark web.
- Malware and Keyloggers Menace: Malicious software and keyloggers capture keystrokes and sensitive information from compromised devices, providing hackers with usernames, passwords, and other credentials without the user’s awareness.
Shedding Light on the Shadows: The Significance of Dark Web Credential Monitoring
In the murkiness of the dark web, a beacon of hope emerges through dark web credential monitoring. This proactive cybersecurity approach involves continuous surveillance of dark web marketplaces, forums, and chat rooms where stolen credentials are traded.
- Continuous Vigilance: Dark web credential monitoring entails constant surveillance, utilizing automated tools to scan for patterns and matches against a database of compromised information.
- Real-time Alerts: Upon detection of compromised credentials, credential monitoring tools promptly send alerts. Immediate notification enables users to take swift action, such as changing passwords or activating two-factor authentication.
- Risk Mitigation in Action: By actively monitoring the dark web for compromised credentials, users and organizations can proactively mitigate potential risks. Identifying stolen information early on prevents unauthorized access, minimizing the impact of a data breach.
In a constantly evolving digital landscape, understanding how user credentials traverse into the dark web is vital. Credential monitoring emerges as a crucial defense, offering a proactive approach to identifying and mitigating risks associated with stolen credentials. In a world driven by interconnectedness, staying vigilant and embracing innovative solutions like dark web credential monitoring is the key to safeguarding digital identities.