In the vast and interconnected digital landscape, the value of stolen data has reached unprecedented heights. Cybercriminals are relentlessly targeting our valuable information with the intention of selling it on the dark web, a thriving marketplace for illicit transactions. As the threat landscape evolves, it is crucial for businesses to understand the nuances of stolen data value and take proactive measures to protect their digital assets. This blog post serves as a guide, emphasizing the importance of categorizing data and initiating awareness training to fortify your defense against data breaches.
Understanding the Value of Stolen Data:
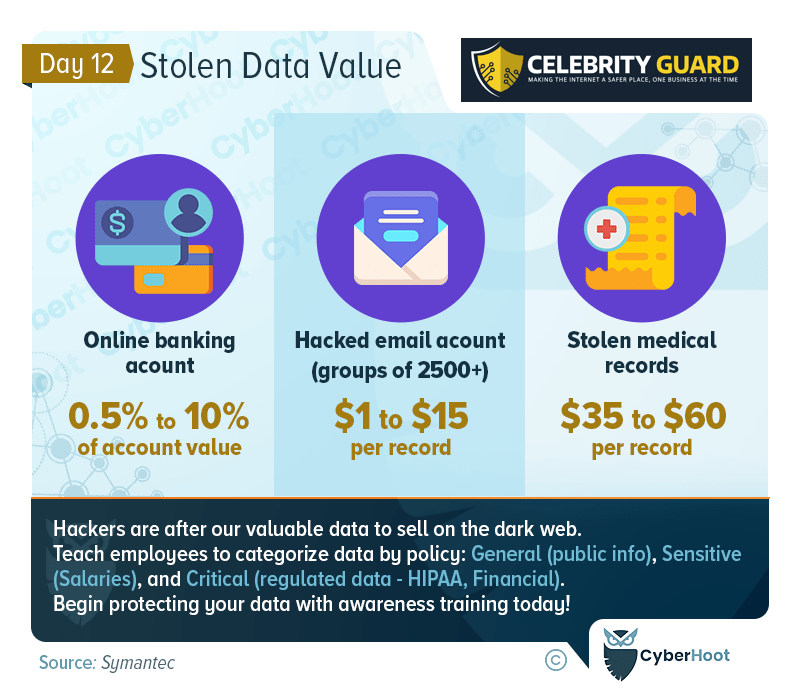
Hackers are not just after random bits and pieces of information; they are specifically targeting data with substantial market value on the dark web. This includes sensitive details such as personal identities, financial records, and proprietary business information. The more valuable the data, the higher the demand on the dark web, making it imperative for organizations to comprehend the true worth of their digital assets.
Teaching Employees to Categorize Data:
To effectively protect against data breaches, it is essential to educate employees on categorizing data according to its significance and sensitivity. Establishing a clear classification system can empower your workforce to handle information appropriately. Consider implementing the following categorization levels:
- Policy General (Public Info):
- Examples: Publicly available information, marketing materials, and general company information.
- Handling: No specific restrictions, suitable for public consumption.
- Sensitive (Salaries, Personal Information):
- Examples: Employee salaries, customer personal information, and proprietary business strategies.
- Handling: Limited access, encryption, and heightened security protocols.
- Critical (Regulated Data – HIPAA, Financial):
- Examples: Healthcare records (HIPAA), financial transactions, and any data subject to legal regulations.
- Handling: Restricted access, robust encryption, and compliance with relevant regulations.
Initiating Awareness Training for Data Protection:
The first line of defense against data breaches is a well-informed and vigilant workforce. Conducting awareness training sessions can empower employees to recognize potential threats, understand the value of the data they handle, and adopt best practices for safeguarding information. Key components of awareness training may include:
- Recognizing phishing attempts and social engineering tactics.
- Implementing strong password policies and multi-factor authentication.
- Understanding the importance of secure communication channels.
- Reporting any suspicious activity promptly to the IT department.
Begin Protecting Your Data Today:
Armed with the knowledge of the value of stolen data and the significance of categorization, businesses can take the first step towards a robust defense against cyber threats. Implementing awareness training for employees not only enhances the overall security posture but also fosters a culture of vigilance and responsibility.
In conclusion, the digital age demands a proactive approach to data protection. By understanding the value of stolen data, categorizing information appropriately, and investing in employee awareness, organizations can create a formidable defense against the ever-evolving threat landscape. Take action today to safeguard your digital assets and ensure the resilience of your business in the face of cyber threats.